Security
Jive leverages multiple layers of defense to protect key information and handle all critical facets of network and application security, including authentication, authorization and assurance.
Jive maintains a highly mature security program, based on industry best practices. While this page provides a high level overview, more detailed information is available to prospects under NDA.
Third Party Certifications and Audits
Third-party certifications and audits are an important component of any mature security program. We have a number of respected third-party agencies that certify and audit our environment.
Jive Security Architecture
Jive’s security architecture is designed to protect the confidentiality, integrity and availability of all customer information that we host. We apply stringent, risk-adjusted security controls in layers ranging from facilities (physical security) to network infrastructure (network security), IT systems (system/host security) and information and applications (application security). Jive has the following security controls:
Secure data centers
Jive leverages Amazon Web Services (AWS) as our datacenter provider of the future. Amazon AWS provides customers with the ability to view their SOC2 Type 2 report. Instructions on registering for, and obtaining this report, are available at https://aws.amazon.com/compliance/soc-faqs/.
Encryption
Jive provides strong encryption options for customers to use, which secures the Data in Transit (DIT) from the client side, to our core services. As part of our migration to Amazon Web Services (AWS), customers also gain the benefit of having all of their data encrypted by AWS, providing Data at Rest (DAR).
Jive AWS Cloud Infrastructure
is designed in accordance with best practices guidelines.
Cookies
More information on how our cookies are used is available at https://docs.jivesoftware.com/.
Security Monitoring
Our networks and systems are continuously monitored for security issues. Security events are correlated for evaluation by our security team, using a Security Information and Event Management System (SIEM) tool.
Application Programming Interfaces (API)
Secure API’s are available for customers, which can be used to export security data to a Security Information and Event Management (SIEM) solution. More information can be found https://community.aurea.com/docs/DOC-112283.
Hardened operating systems
All operating systems are configured to only use the minimal number of required services.
Includes strong third-party auditing in the form of our SOC2
Everything is audited (internally and by 3rd parties)
Separated services
All services are isolated and not shared, minimizing the risk of unintended data disclosure.
Strict access controls
Jive enforces strict access control on all its systems. We perform regular internal audits and use automated tools to verify desired configurations.
Strict ingress and egress points
Access to the application is restricted to ports 80/443. Jive administration is limited to a small group of Jive workers using a secure 2-factor VPN to access customer environments. All activity is logged.
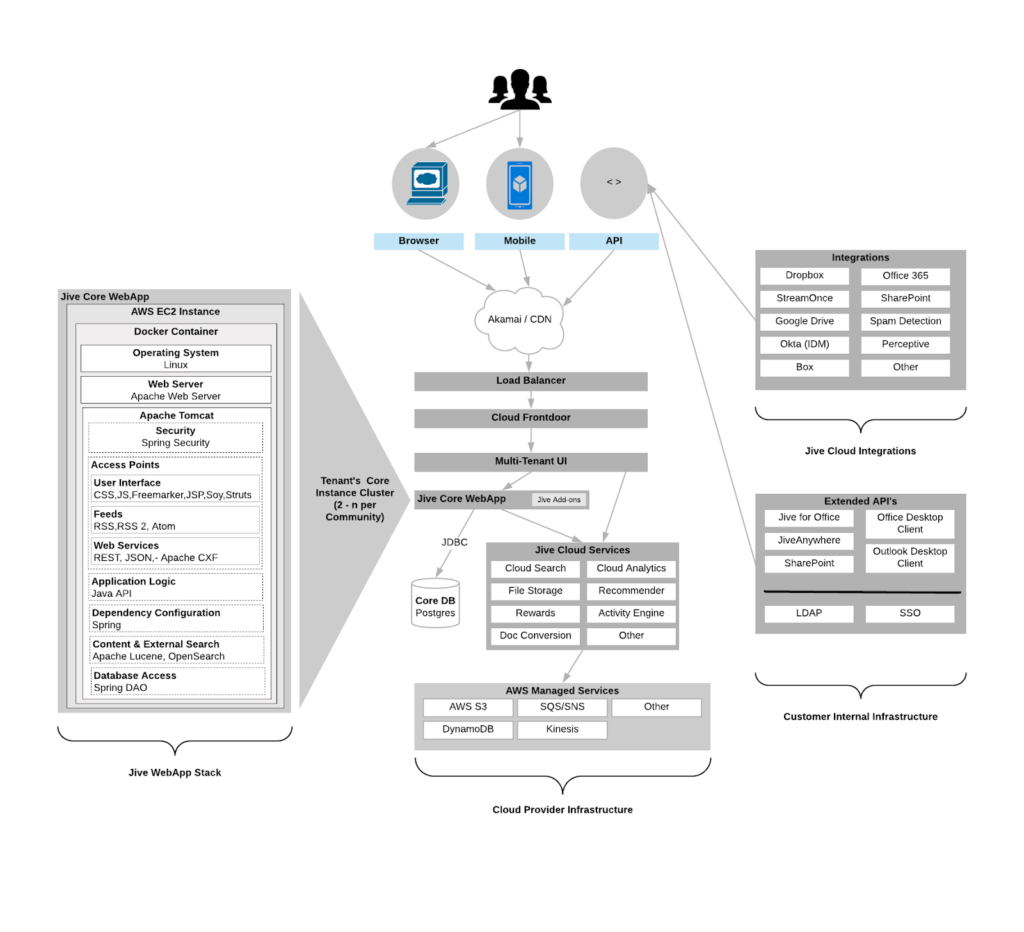
Security Architecture
The following diagram represents the Jive security architecture using standard AWS components. The Jive production network is completely segregated from the Jive corporate network. During the migration phase, some services may exist in the Jive data centers and others on AWS.
Data Security
All of our security controls and risk analysis are based around the premise of protecting customer data. Jive hosting supports various encryption methods to protect data transiting over untrusted networks. Customers can choose to implement SSL or VPN technology to add a layer of protection to their hosted site. Encryption has also been implemented for both transit and storage of offsite backups in the remote data center facilities.
Restricted access to customer data
Jive’s access to customer data is highly restricted, and access requests by our support personnel follows a highly controlled and documented process. Before access is granted, employees must complete special security training to handle customer data.
Incident and response
Jive has an incident response process designed to handle customer data incidents.
Logging and audit
All activity is logged in a protected system and is audited using automated tools.
Training
All Jive employees are required to participate in security training.
Software Engineering Security Process
Security is continuously improved and tested throughout the Jive product lifecycle. All new feature designs are audited for high-level security considerations, and feature implementations are checked for security flaws throughout development. Existing features are audited for security vulnerability regressions, and application-wide audits are performed to ensure that feature integration is secure. Third-party components used by Jive are researched and monitored carefully for vulnerabilities. Jive has a security team focused on application security testing, using both manual and automated methodologies.
Certified Security Personnel
Jive’s Security team includes certified Information Security professionals with expertise in application, network and architecture security who help define our security policies and security controls. The Jive security team is composed of professionals with graduate-level degrees, 10 years industry experience, and security certifications including CISSP, CISA, CRISC, ITIL v3, and ISO 27001 Lead Auditor.
Best Practices
Jive maintains secure programming best practice documents based on OWASP requirements. Best-practice documents are updated on a regular basis to reflect current vulnerability knowledge, and also provide developers with real-world examples of previous programming mistakes and how to avoid them. Topics covered include input/output data sanitation, proper usage of authentication and authorization, avoiding information disclosure and secure file system (and other resource) usage.
Jive engages trusted third-party testers to perform a comprehensive security review of its product, based on OWASP standard methodologies. OWASP Top 10 Project, CWE and the SANS Top 25 Most Dangerous Software Errors are analyzed.
Such tests include:
- Application discovery and reconnaissance
- Identification of weak point
- Penetration testing using tools and techniques that mimic malicious attackers
- Reporting of vulnerabilities
- Patch verification
Applications Security Process
Security Assessment Policy
Jive’s release readiness workflow includes continuous security tests and assessments. Manual and automated security tests are conducted at critical milestones, prior to public release. Security vulnerabilities discovered during these tests are then reviewed for criticality, and assigned to Engineering for resolution. Based on criticality, the issue may be resolved prior to release, or addressed in a future update.
Managing Vulnerabilities
Jive conducts continuous vulnerability scanning of our cloud and hosted environments, and has a Patch and Vulnerability Policy that provides oversight of our patching process. Customers are free to install the security patches in an on-premise instance, and the hosting team is available to apply security patches per customer requests. Jive leverages US-CERT alerts, open source data and internal testing to identify potential vulnerabilities. Remediation efforts are prioritized based on the risk level calculated by the Common Vulnerability Scoring System (CVSS).
Product Security Features
The Jive platform has a number of built-in features for configuring security at a level appropriate to your organization. Our Professional Services team is available to perform customizations on your instance, if the out-of-the-box options don’t meet your security requirements.
Tools
Jive utilizes best-in-class security tools to monitor our environment, such as:
- Intrusion Detection Systems (IDS) monitoring
- Distributed Denial of Service (DDoS) detection and mitigation
- Security Information and Event Management (SIEM) logging and analysis
- Web Application Firewall (WAF)
- Application security scanning, using multiple products
Availability
Jive strives to maintain excellent uptime for our customers. Instance-specific uptime reports are available for review, on a monthly basis.
*Definition of availability: The solution is available if Jive can complete the following tasks using its automated metric calculation tools:
- Access the home page of the administrative interface for the community and confirm correct rendering of the page,
- Log into the solution using the Private Jive Account (i.e., no SSO login) and confirm correct rendering of the page,
- Navigate to the community landing page and confirm correct rendering of the page.
Privacy
Our commitment to privacy is second to none in the industry. When it comes to protecting the data that our customers, partners and website visitors entrust to us, we make no compromises. The following certifications attest to our best-in-class privacy program.
Certifications by Third-Party Data Compliance Services Provider
GLBA
The Gramm-Leach-Bliley Act (GLBA) is a United States federal law that requires financial institutions to explain how they share and protect their customers’ private information Jive’s assessment is based on a third party audit of controls found in the Federal Financial Institutions Examination Council (FFIEC) IT Security Handbook To ensure GLBA compliance, Jive engages a 3rd party audit firm to assess controls and issue a report. These reviews occur biennially.
Hipaa
Jive provides information technology solutions for entities that are considered Covered Entities under the Health Insurance Portability and Accountability Act of 1996 (“HIPAA”). To ensure HIPAA compliance, Jive engages a 3rd party audit firm to assess controls and issue a report. These reviews occur biennially.
GDPR Compliance
On 25 May 2018, the General Data Protection Regulation (GDPR) took effect in the European Union (EU). The new regulation imposes broad new data privacy protections for EU individuals and applies to any company that collects or handles EU personal data. Jive is committed to helping our customers comply with the GDPR through privacy and security protections in our products and services. We have taken steps to implement GDPR-compliant functionality in our Jive Interactive Intranet product. The new features are supported in Jive cloud, hosted, and on-premise software deployments. More information can be found in Jive’s GDPR whitepaper.

